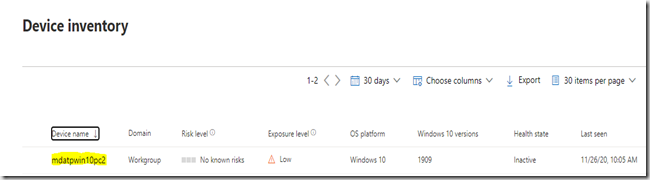
L’objectif est identique à l’intégration via un script local, traité dans un récent article mais dans cet exemple l’ intégration s’effectue en:
- Ajoutant sur la machine cible le compte de l’utilisateur de la machine tel qu’il apparait dans Endpoint Manager
- S’assurant de la configuration du connecteur entre Endpoint Manager et Defender ATP (action à effectuer une seule fois)
Créant un profil de configuration dans Endpoint Manager pour permettre à la machine de s’enregistrer sur Defender ATP.
1. Ajout du compte du user pour inscription dans Windows Intune et découverte du device:
sur le client Windows 10,ouvrir « Access Work or School »
Connect
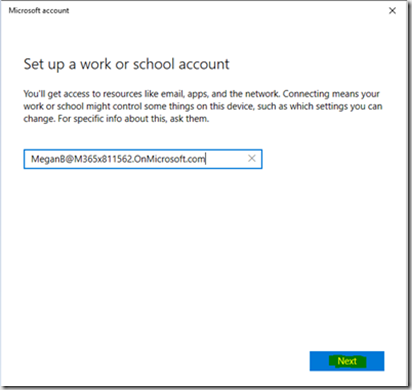
Renseigner le compte du user O365 et cliquer Next
Renseigner le password du user.
2. Option Intune activée dans Defender Security Center
Dans la console Defender Security Center aller dans Setting /Advanced Features
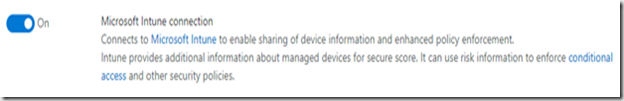
S’assurer que l’option Microsoft Intune connection est bien On
3. Types d’OS autorisés
Dans la console Endpoint Manager aller sur Endpoint Security / Microsoft Defender ATP
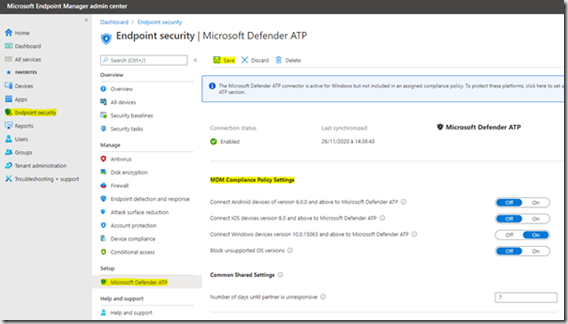
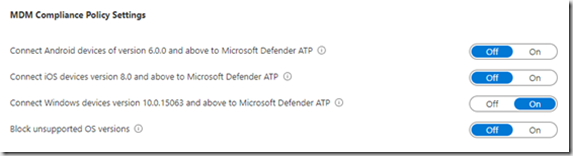
Dans la zone MDM Compliance Policy Settings’, s’assurer que les types d’OS devant etre connecté sont bien autorisés.
4. Creation d’une Configuration Policy dans Endpoint Manager
- Dans la console Endpoint Manager aller sur Devices / By Platform : Windows / Configuration profiles
NB : L’objectif est de créer une/des ‘Configuration Policy’ qui vont permettre aux devices de s’enregistrer.
Des configuration Policies similaires peuvent etre crées pour les autres type de device (Devices / By Platform)
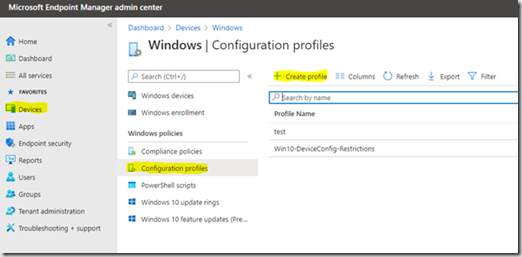
Cliquer Create Profile
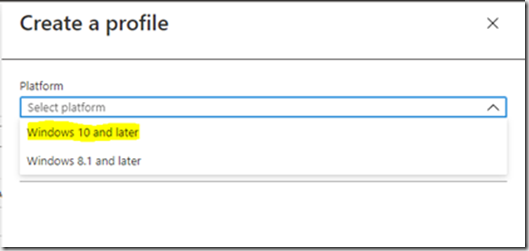
Selectionner Windows 10 and later.
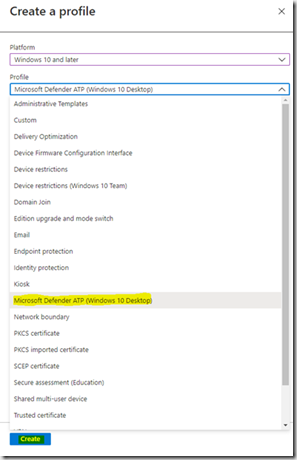
Selectionner ‘Microsoft Defender ATP (Windows 10 Desktop)’ puis Create.
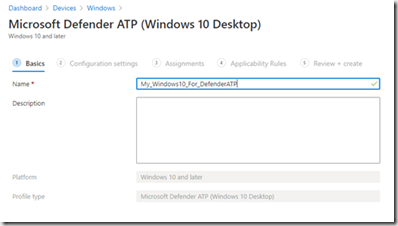
Nommer la Policy avec un nom explicite
Cliquer Next
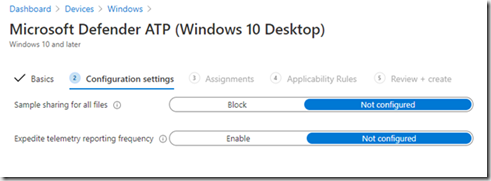
Laisser ces options Not Configured
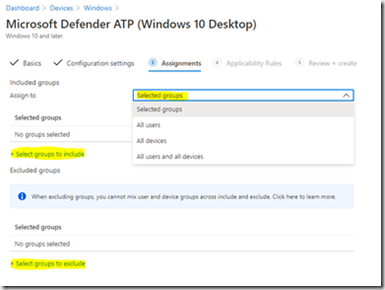
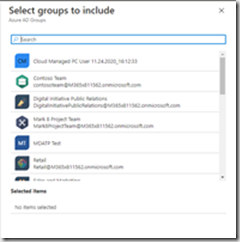
Dans cette zone il s’agit de sélectionner le scope des devices/users a qui va s’appliquer la policy.
Si un/des groupes crées dans Endpoint Manager auparavant, doivent être sélectionnés, cliquer Select groups groups to include.
Sélectionner d’éventuels groupes à exclure.
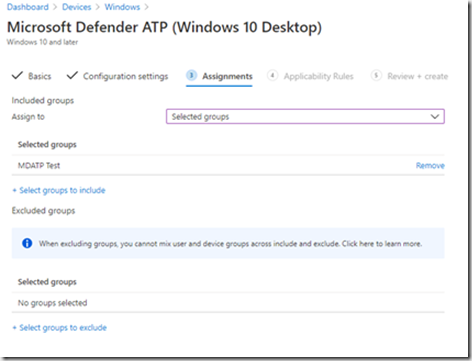
Cliquer Next
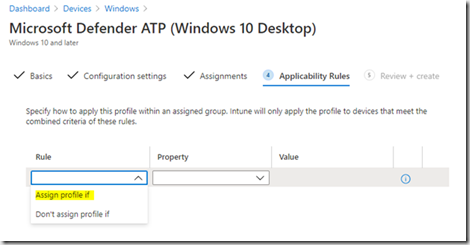
Selectionner la règle d’application (NB : les règles d’application sont differentes selon les types de devices et profile)
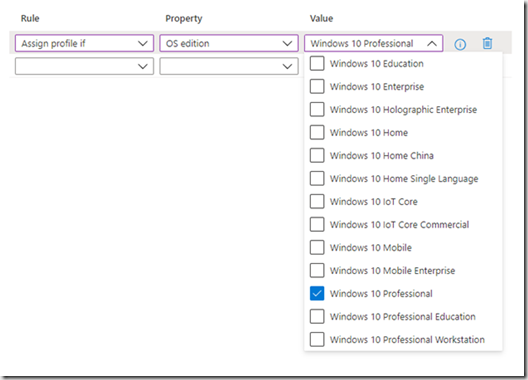
Dans cet exemple on applique le profile SI l’édition de Windows 10 est ‘Windows 10 Professional’
Cliquer Next.
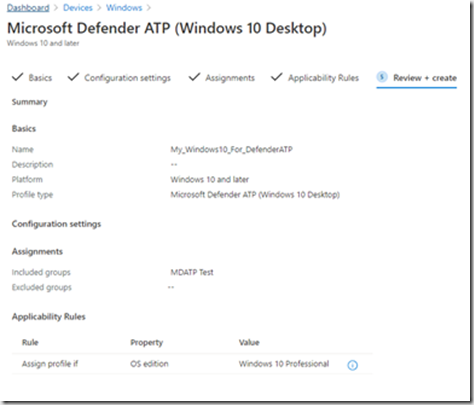
Résumé de la création.
Cliquer Create.
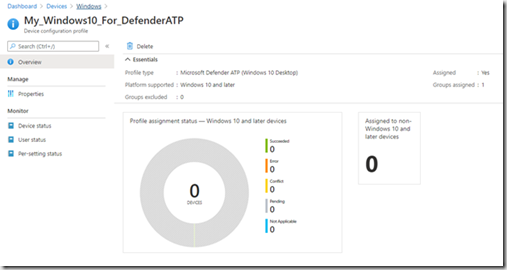
A l’issu de la création un dashboard affiche le statut de l’assignation du profile.
Pour le moment le dashboard affiche 0. Le deploiement est en cours.
NB : Penser à vérifier que le groupe crée au préalable contiens bien des objets auxquels le profil doit être appliqué.
Il est également possible de cliquer sur Properties ( ) pour afficher les propriétés de la policy crée et notamment le/les scopes. (groupes/users)
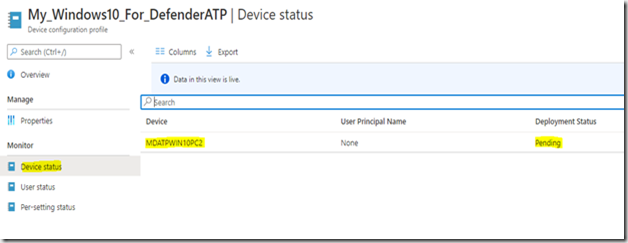
Contrairement au dashboard, la zone Monitor affiche immédiatement le contenu (ici la machine de test qui est membre du groupe que l’on a associé à la policy (groupe de test ‘MDATP Test’) :
Et l’on peut voir que le champ Deployment Status affiche ‘Pending’ :
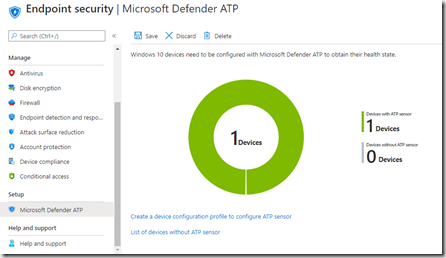
Des que la policy est deployée, on retrouvera la machine cible dans les devices “with ATP Sensor”
Et surtout, dans la console Defender Security Center.