Introduction
Powershell 5.0 est encore en beta mais de nombreuses nouveautés sont déjà présentes. Nous allons aborder dans cet article quelques unes d’entres elles. Elles peuvent concerner : Powershell, son éditeur (Powershell ISE) ou encore son paramétrage dans Windows. Certaines avaient déjà été évoquées dans l’article suivant lors de la première preview de Powershell 5.0 :
http://blog.piservices.fr/post/Powershell-V5-Preview-est-sorti-!-DSC-Switch-OneGet-et-du-chocolat.aspx
NB : Contrairement à la première beta, Powershell 5.0 est dorénavant disponible pour Windows 2012 et supérieur (qui n’était compatible qu’avec Windows 2012 R2 et supérieur). Le lien suivant vous mènera à la dernière beta sortie (Novembre 2014) :
http://www.microsoft.com/en-us/download/details.aspx?id=44987
Gestion des Archives
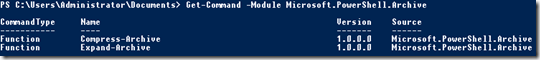
Un nouveau module permettant de gérer nativement les archives apparaît dans Powershell 5.0. Cette option n’était auparavant disponible qu’au travers de module réalisé par la communauté. Ce dernier permet de générer des archives (Compress-Archive) ou de les extraire (Expand-Archive). Seul le format Zip est actuellement géré. Un paramètre nommé “update” permet de mettre à jour une archive existante en ajoutant seulement les nouveaux fichiers et les changements sur les fichiers déjà présents dans l’archive. Le paramètre “path” peut définir un ou plusieurs fichiers ainsi qu’un dossier entier en utilisant le caractère “*” (wildcard). Enfin le paramètre “CompressionLevel” permet d’influencer le taux de compression et la taille finale de l’archive.
Support des raccourcis claviers
La console Powershell supporte désormais certains raccourcis clavier : copier (CTRL+C), coller (CTRL+V), tout sélectionner (CTRL+A).
Gestion des liens symboliques
Il est dorénavant possible de créer/supprimer des raccourcis via Powershell. Cette fonctionnalité est incluse dans la commande New-Item en spécifiant le type “SymbolicLink”.
Création d’un raccourci vers un fichier
Création d’un raccourci vers un dossier
On peut aussi lister des fichier via la commande Get-ChildItem en passant par un raccourci !
Event Viewer
Un nouveau journal de log est apparu dans l’observateur d’événements. Par défaut, ce dernier enregistre les lancements de console Powershell et les erreurs générales comme un échec de chargement de module. Ce nouveau journal est situé dans Applications and Services Logs\Microsoft\Windows\PowerShell\Operational. Il peut aussi enregistrer les exécutions de code Powershell. Cette fonctionnalité s’active via GPO.
Attention : Activer l’utilisation de ce journal pour les exécutions de code est très verbeux. Néanmoins cela peut être très utile pour obtenir rapidement des traces d’actions effectuées sur des serveurs via Powershell.
Il est possible d’activer cette fonctionnalité via GPO (voir paragraphe ci-dessous).
GPO
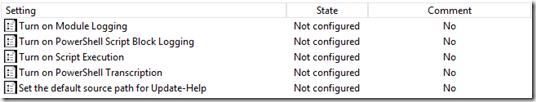
Les modèles d’administration possède désormais un ADMX permettant de gérer quelques paramètres Powershell. Ce dernier est situé dans Administrative Templates / Windows Components / Windows PowerShell. Il serait compatible avec les systèmes d’exploitation de la famille Windows 7 / Windows 2008 et supérieur (je ne l’ai personnellement testé que sur Windows 10 Server Technical Preview). Cette nouveauté n’est donc pas totalement liée à Powershell 5.0 puisqu’elle sera fonctionnelle sur les anciennes versions de Powershell.
Les paramètres configurables sont les suivants :
-
Activer les traces dans l’observateur d’événements pour tout exécution de script.
-
Activer les traces dans l’observateur d’événements pour les exécutions de module Powershell (il faut préciser les modules concernés).
-
Définir la politique d’exécution des scripts (Set-ExecutionPolicy). Il s’agit d’une très bonne nouvelle car il n’existait pas de solution pour généraliser ce paramètre sur un grand nombre de serveur hormis en passant par une ressource DSC (ce qui représente un déploiement beaucoup plus lourd).
-
Activer automatique du transcript : cela permet de ne pas avoir à lancer la commande “start-transcript”. Il est également possible de définir le chemin où doit être stocké le transcript. Par défaut le nom du fichier est horodaté, contient le nom de l’ordinateur et est stocké dans le répertoire “Mes documents” de l’utilisateur de la session Powershell.
-
Définir la source de l’aide Powershell. Depuis Powershell 3.0, l’aide des cmdlets n’est pas entièrement incluse avec le package d’installation Powershell. Il est nécessaire d’utiliser la commande “Update-Help” pour la mettre à jour (par défaut, elle est récupéré depuis internet). Cela permet entre autre de récupérer l’aide avec la langue qui nous intéresse. Grâce à ce paramètre, on peut dorénavant spécifier une source comme un partage de fichier. Néanmoins, l’utilisateur a toujours la possibilité de changer le comportement en indiquant lui même une valeur lors de l’exécution de la commande via le paramètre “SourcePath”.
Tous ces paramètres sont disponibles dans la configuration ordinateur et utilisateur de la GPO.
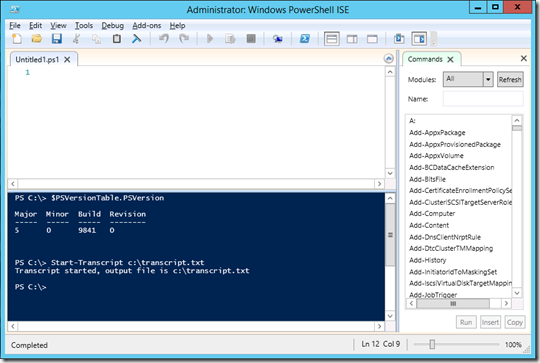
Transcript
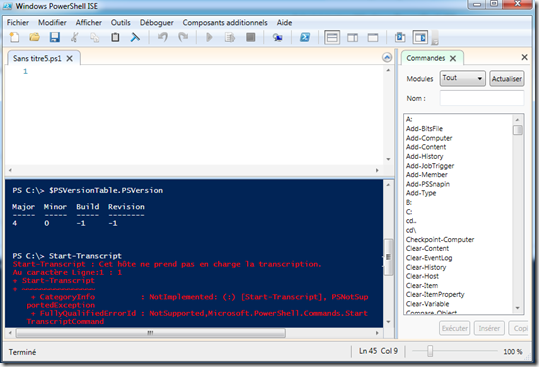
La génération de transcript n’était jusqu’à présent fonctionnelle que dans la console Powershell. Grâce aux cmdlets “Start-Transcript” / “Stop-Transcript”, il est désormais possible de générer des fichiers de traces aussi via Powershell ISE.
Powershell ISE avec Powershell 4 :
Powershell ISE avec Powershell 5 :
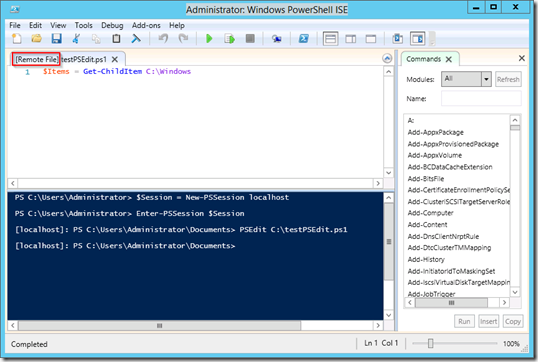
PSEdit
Une nouveauté fait son apparition dans Powershell ISE et le PSRemoting : PSEdit. Cet outil existait déjà et permettait d’ouvrir script dans un nouvel onglet dans Powershell ISE lorsque l’on exécutait la commande suivante : PSEdit chemin_de_mon_script.
Cependant, dans cette nouvelle version de Powershell ISE, il est possible d’ouvrir des fichiers à distances. Il n’y a donc plus besoin d’ouvrir Powershell ISE sur la machine où se trouve le script pour l’éditer. Il suffit d’ouvrir une PSSession puis d’exécuter PSEdit.
Cette fonctionnalité est facilement testable même en local en simulant une session distante :
Il n’y a pas besoin de connaître le chemin exact du script puisque l’auto complétion est disponible pour le retrouver.
Enumérations
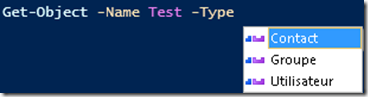
La dernière nouveauté expliquée dans cet article est plus orientée scripting. Les énumerations font leurs apparitions dans Powershell. Pour cela un nouveau mot clé est disponible : “enum”. Celles-ci vont nous permettre de réaliser plus rapidement de la validation de paramètres.
Prenons le cas du paramètre ErrorAction disponible sur toutes les commandes Powershell. Il n’est possible de fournir qu’un certain nombre de valeurs : Continue, Ignore, Inquire, SilentlyContinue, Stop, Suspend. Ceux-ci correspondent à une énumération.
La syntaxe d’une énumération est la suivante : Pour utiliser cette dernière dans une fonction :
Nous pouvons remarquer que les choix disponibles sont proposés par le système d’auto complétion.
 Enfin, si l’on souhaite récupérer les valeurs d’une énumération, il faut exécuter la commande suivante :
Enfin, si l’on souhaite récupérer les valeurs d’une énumération, il faut exécuter la commande suivante :
Conclusion
Powershell 5.0 et Windows 10 sont riches en nouveautés pour le langage de scripting de Microsoft. Certaines d’entre elles n’ont pas été abordées mais feront l’objet d’articles dédiées :
-
La création de classes d’objets personnalisés.
-
Les améliorations de Desired State Configuration comme la gestion des configurations partielles permettant de segmenter celles-ci en plusieurs fichiers (exemple : par fonctionnalité).
-
PowershellGet : à l’instar de OneGet qui permet de récupérer des packages, ce dernier offre la possibilité de récupérer des modules depuis internet ou depuis sa propre source. Ainsi, une société peut créer sa bibliothèque de modules Powershell.

0 commentaires